Anonymity is soon becoming extinct with the digital age. With social plugins and log activities, it has become nearly impossible to protect one’s privacy and one’s identity. However, the bright side is that the progress in the capability of internet usage is being made in both directions. So while there are sinister individuals bearing malicious intentions, there are also those IT specialists who are striving to offer internet privacy to users.
What is TOR?
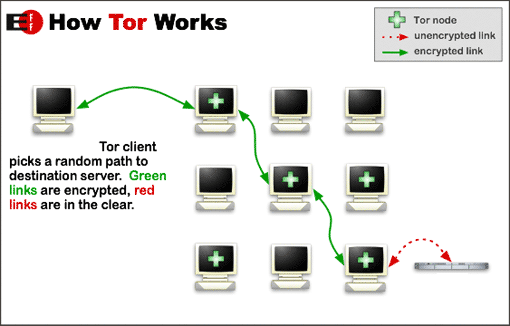
TOR stands for The Onion Router and is a free software (both as in free speech and free beer) that offers protection to you by juggling your communications within a relay network that is run by volunteers from across the globe. By directing Internet traffic through more than six thousand relays, TOR can offer protection and concealment of user’s location and user activity from those conducting a traffic analysis or network surveillance.
In simple terms,
- It can prevent any other person to have remote access to your private internet usage information.
- It can stop sites that you visit from gaining access to your physical location.
- It also lets you access blocked sites.
So, what you do on the internet and through your browser now stays your private information.
What is TOR Browser?
Literally a browser that lets you use TOR on Mac OS X, Linux or Windows without requiring a download of a particular software other than the Tor Browser.
Here are some properties of the Tor browser:
- It can even run from a USB flash drive, it can be portable.
- It is self-contained, no additional software required.
- It has a pre-configured web browser with special settings to offer further protection to privacy and anonymity; you can disable websites' scripts.
Why is it Important to Use TOR?
Traffic analysis is a common form of internet surveillance. Although at most times it could be harmless, yet at some occasions where this analysis is meant to creep into the private information of an individual, it can even infer who is talking/chatting to whom and even vital information like identification codes, physical location and financial standing.
At the time of using the internet, users leave their track all over web. For example, every time the users visit the website, their IP address (which is the computer’s ‘address’) will be logged and the websites will also save information regarding the browsers they are using and even the time they spend on the website and the links that were visited.
By downloading TOR browser 4.5.1, you can attempt to protect your privacy and hence keep your anonymity.
What are the new features of TOR Browser 4.5.1?
TOR Browser 4.5.1 was released a few days ago and introduces some tweaks.
Indeed, TOR Browser 4.5.1 is based on the updated Firefox ESR 31.7.0.
You may ask yourself what is Firefox ESR ? Simply put, it's a special Firefox edition made for people who don't want the latest, bleeding edge features, new technologies, and performance enhancements, but instead need an Extended Support, that is to say, it's updated less often, but its end of life is further in time, it receives updates for longer.
This new Firefox ESR version corrects several security vulnerabilities, including a critical one that could 'be used to run attacker code and install software, requiring no user interaction beyond normal browsing.'
To be fair, TOR browser 4.5.1 is mainly a refinement of the 4.5 release.
New features of TOR Browser 4.5
As you can read on the official TOR blog post, TOR browser 4.5 brought improvement in three domains: usability, security, and finally privacy.
1) Usability Improvements
Until now, when you installed the TOR browser on Windows, by default, it sat in a folder on your desktop, without any further integration with the Windows OS. But that has now changed with the 4.5 release, which introduce much needed little things such as shortcuts in the Start menu (or the Applications view on Windows 8). Of course, it's an option you can disable in the case of a portable installation
The Green Onion menu in the browser has also been simplified now display your current TOR circuit in the onion network.
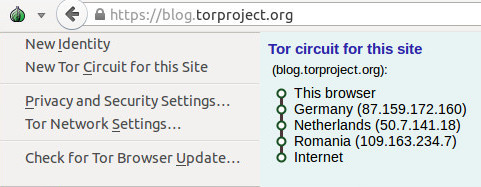
They also made changes under the hood in the way TOR browser handles TOR circuit in general : now, the TOR circuit used for a site shouldn't change in the middle of your browsing session, eliminating the jarring language changes that could happen in the past.
2) Security Improvements
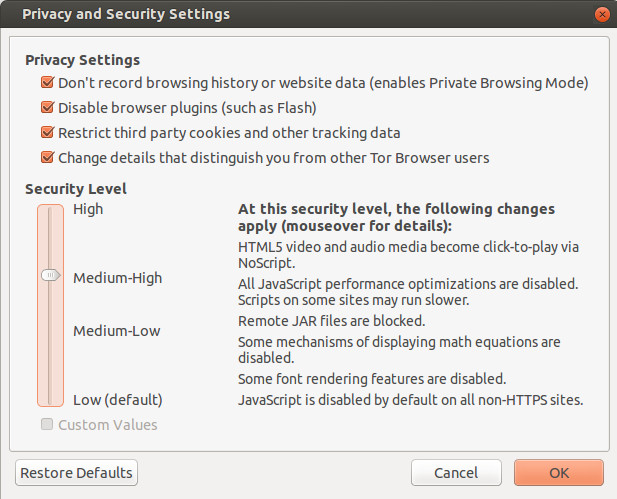
The biggest change in the TOR browser 4.5 branch is the new Security Slider which allows you to set simply your security settings in a way similar to Internet Explorer.
Another notable change is the new DigiCert signed installation package. Before that, when you installed TOR browser on Windows, there was a warning about 'unknown sources'. With the new certificate, you can be sure you downloaded the official TOR browser and not a modified copy.
There's also a rewrite of the underlying encryption mechanisms of TOR browser, namely obfs2,obfs3, ScrambleSuit transport and obfs4 (more resistant to probing).
3) Privacy Improvements
TOR Browser 4.5 introduces a new feature called First Party Isolation to prevent the nasty tracking from spying on you. With First Party Isolation, social sharing buttons (Facebook Like, Google+ +1, Twitter Tweet) and other trackers can only track you on the website there are, not accross websites over the whole Internet.
Why TOR Browser isn't the best privacy protection
However, the TOR Browser has several drawbacks that prevent it from becoming an ultimate privacy protection, compared to VPN services:
1. TOR Relays can be malicious
When your connection is relayed through volunteers' computers that are part of the TOR network, there is always the small risk of having your information passing through a rogue relay, that could spy on your traffic, as noted by a PCWorld article dated of January 2014:
Even though connections between Tor relays are encrypted, traffic is returned to its original state when it leaves the network. This means that if it’s not using SSL or another secure transport protocol, Tor exit relays can inspect it.
A TOR exit relay is the final computer in the onion routing, the one that retrieves the webpage that your TOR browser has asked. That's why a rogue relay can be dangerous, unless you use SSL connections: not only it can inspect your traffic, but it can also modify it, inject malware on the pages you visit, or even in your downloads as it happened in November 2014 with the OnionDuke APT Malware discovered by the Finnish security company F-Secure.
But that's not the only risk associated with using the TOR browser...
2. Plugins can give away your real IP (your location)
TOR browser is just a browser. So it in fact uses a Proxy, with a weaker encryption than the standard VPN protocol, OpenVPN. But there's another threat: plugins. Even though Apple has done everything to make Adobe Flash obsolete, numerous websites still rely on it for animated contents, videos... And Flash is not proxied when you're using TOR. And it's the same story with Java. Of course, Java has lots of vulnerabilities on its own, but it doesn't play ball with TOR browser either. And the plugins like Java, Real Player, QuickTime and others can be manipulated through exploits to give away your true location and identity.
3. Your downloads betray you
When you download a file with the TOR browser, you download them with your IP hidden by the TOR onion network. But if you open them with an external application, like Adobe Reader or Word, the internet-resources they contain (i.e. images) will call home and they will be downloaded with your real, non-TOR IP address, thus exposing it.
However, not everything is dark in the TOR world. If you're ready to recycle a USB key for TOR, you could significantly improve your protection.
Tails, a Live OS on your flash key for your privacy
Even though the TOR project's flagship product is the TOR Browser, there is something even more secured based on it. Tails, acronym for The Amnesic Incognito Live System, is a complete operating system (like Windows), that you can install on a USB key. When you boot from this key, Windows (or your regular OS) doesn't start, and instead it's a Linux-based OS with only TOR browser and other security tools that boots.
Tails is super-secured, and it was even used by Edward Snowden to evade the NSA.
Any Questions Left?
What do you think of TOR? Do you use it? What other tools are you using? Tell us in the comments just at the bottom of this page.







