The U.S. government announced it had darkened a key domain related to VpnFilter, a sprawling malware botnet that in recent days had hacked over 500,000 routers and other devices in 54 countries.
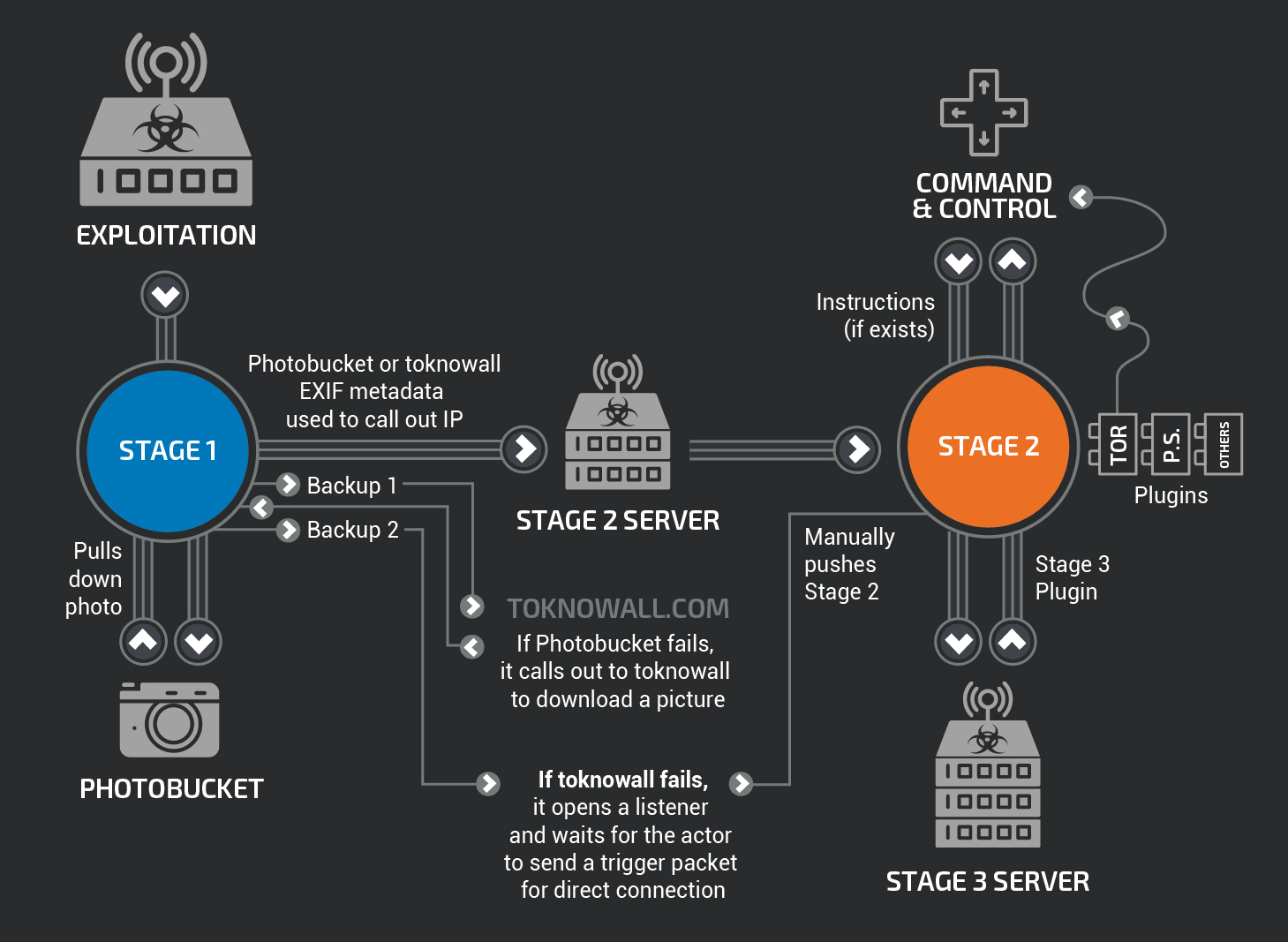
Initially detected by the Cisco Talos Intelligence Group, the malware breached routers from manufacturers such as Linksys, MikroTik, Netgear, Tp-Link, and Qnap NAS. In short, it had created a world 'army' of devices able to filter and control the network traffic passing through, thus stealing private data and information and communicating through the anonymous TOR network. It even performed fatal actions causing the self-destruction of infected devices: overwriting critical parts of the devices' firmware and forcing a reboot, effectively bricking them.
In particular, it seems that the exploit, i.e. the execution of the malicious code, was divided into two phases.
First with the infection and forced reboot of the devices then the interception and recovery of files and sensitive information. Also in this second phase would be included the command able to start the self-destruction of the router. A code, the experts noted, very similar to that of BlackEnergy, the Trojan that conducted DDoS computer attacks (therefore a different product from VpnFilter) of the cyber attacks in Ukraine between 2014 and 2016, also managing to 'turn off' three power plants in the country.
VpnFilter was dealt a fatal blow with the shutdown of the ToKnowAll(.)com domain, connected to the central malware server and thus the essential hub of this massive botnet consisting of routers, servers and NAS. By cutting communication with the site in question, the FBI has been able to 'free' most of the compromised devices.
By taking control of the malware command and control server, diverting the virus requests to its own controlled server and thus acquiring the IP addresses of the infected routers, which were then transmitted to the authorities of the various countries.
The advice for those who have those routers is to reboot them, disable remote access, update the firmware and protect it with a firewall. The models involved are listed here, even though the list is believed to be far from complete as more models could be impacted.
- Linksys E1200
- Linksys E2500
- Linksys WRVS4400N
- Mikrotik RouterOS for Cloud Core Routers
- Versions 1016, 1036, and 1072
- Netgear DGN2200
- Netgear R6400
- Netgear R7000
- Netgear R8000
- Netgear WNR1000
- Netgear WNR2000
- QNAP TS251
- QNAP TS439 Pro
- Other QNAP NAS devices running QTS software
- TP-Link R600VPN




