Researchers from the Israel-based Check Point Software Technologies discovered a new vector of attack that puts at risk hundreds of millions users of the most popular media players, including VLC, Kodi (formerly XBMC), Popcorn Time, and Stremio. If you like watching series and movies with these players, you are at risk. But how? The answer lies in the automatically downloaded subtitles.
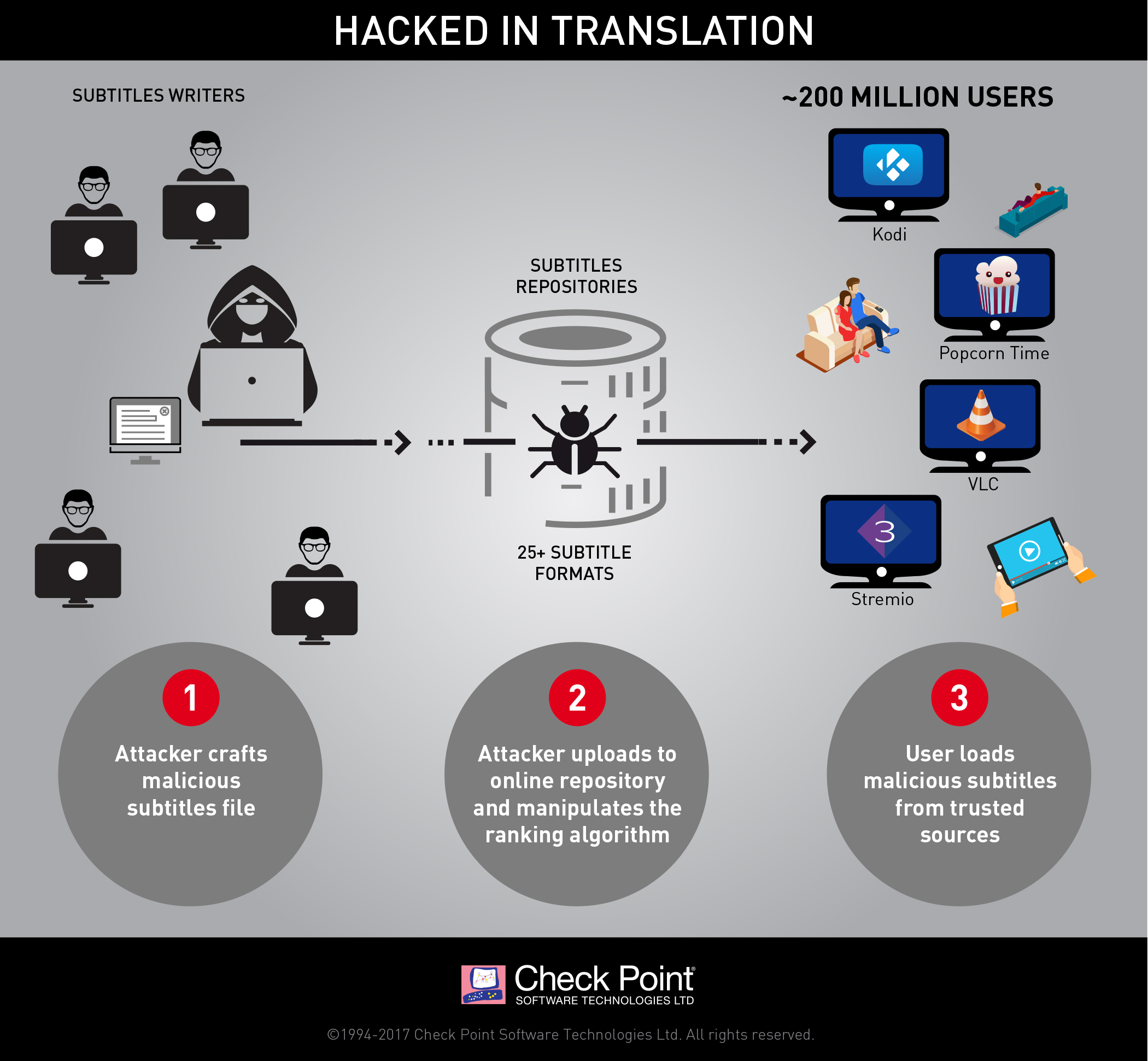
Hackers craft malicious subtitles, upload them to OpenSubtitles and manipulate the ranking of the website to make their booby-trapped subtitles appear to be the most reliable and faithful ones. By downloading these subtitles, users load them into the media player and the exploit makes use of vulnerabilities to take control of devices, with VNC-like technologies.
As this is a serious set of security vulnerabilities, most of the impacted media players released fixed versions. If you use any of these media players, you should update now.
- VLC Update: officially fixed and downloadable through the official website.
- Kodi v17.2 and 17.3: officially fixed and downloadable through official website. Play Store and Windows Store versions will be updated shortly.
- PopcornTime: fixed version is not yet downloadable on the official website, but you can get it here.
- Stremio: officially fixed version can be found on the website.
Affected devices
The attack can be successfully carried out on any device running the media players: PCs, smartphones, tablets, and even Smart TVs.
With this attack, hackers can perform a complete takeover, and do whatever they want on your machines: steal your personal data, install ransomware, launch DDoS attacks.
How did it happen?
The attack relies on the fact that media players support a large variety of subtitle formats. There are over 25 subtitles formats, and each one of them has a unique set of features. This fragmentation, along with the poor security of subtitles repositories, created the ideal conditions for this new type of attack.
Indeed, subtitles repositories are considered as trusted sources by media players. Moreover, to most antivirus products, subtitles are nothing but harmless text files. More often than not, antivirus engines simply skip them.
Most attacks rely on tricking users into running malicious files on their devices or visiting malicious websites. But this new type of attack requires virtually no user interaction, which makes it even more dangerous.
Here is a Proof of Concept video to demonstrate how a hacker can use malicious subtitles to get complete control over your devices.







